What Is SELinux?
What is SELinux?
Why should I use SELInux on my CentOS or Red Hat Enterprise Linux server running on IBM hardware?
SELinux is an acronym for Security-enhanced Linux. It is a security feature of the Linux kernel. It is designed to protect the server against misconfigurations and/or compromised daemons. It put limits and instructs server daemons or programs what files they can access and what actions they can take by defining a security policy.
SELinux puts restrictions on each of the above object according to a policy. For example, an apache user with full permission can only access /var/www/html directory, but can not touch other parts of the system such as /etc directory without policy modification. If an attacker managed to gain access to sendmail mail or bind dns or apache web server, would only have access to exploited server and the files normally has access as defined in the policy for the server. An attacker can not access the other parts of the system or internal LAN. In other words, damage can be now restricted to the particular server and files. The cracker will not able to get a shell on your server via common daemons such as Apache / BIND / Sendmail as SELinux offers the following security features: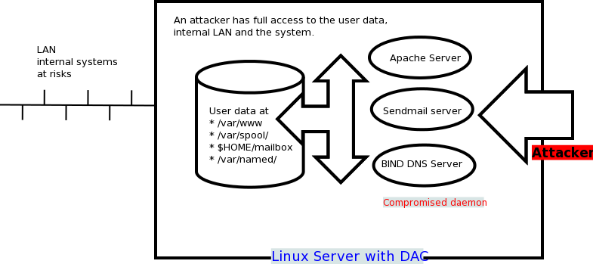
- Protect users' data from unauthorized access.
- Protect other daemons or programs from unauthorized access.
- Protect network ports / sockets / files from unauthorized access.
- Protect server against exploits.
- Avoid privilege escalation and much more.
The SELinux Decision Making Process
When a subject, (for example, an application), attempts to access an
object (for example, a file), the policy enforcement server in the
kernel checks an access vector cache (AVC), where subject and object permissions are cached. If a decision cannot be made based on data in the AVC, the request continues to the security server, which looks up the security context of the application and the file in a matrix. Permission is then granted or denied, with an avc: denied message detailed in /var/log/messages
if permission is denied. The security context of subjects and objects
is applied from the installed policy, which also provides the
information to populate the security server's matrix.
Refer to the following diagram:

Centos – set selinux permissive without reboot
You can view the current mode SELinux operates in, by executing the sestatus comman:
You can change the mode by editing the file /etc/selinux/config and change the SELINUX=enforcing line to SELINUX=permissive
man pages gives this as usage:
to change SELinux currend mode to permissive.
No more reboots and downtime because of selinux!!!
# sestatusYou can change the mode by editing the file /etc/selinux/config and change the SELINUX=enforcing line to SELINUX=permissive
# vi /etc/selinux/config# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
# disabled - No SELinux policy is loaded.
SELINUX=permissive
# SELINUXTYPE= can take one of these two values:
# targeted - Targeted processes are protected,
# mls - Multi Level Security protection.
SELINUXTYPE=targeted
By executing once again the sestatus command you ‘ll get the output:
# sestatusSELinux status: enabled
SELinuxfs mount: /selinux
Current mode: enforcing
Mode from config file: permissive
Policy version: 24
Policy from config file: targeted
My way to change the current mode is to reboot the machine. Today I
discovered that you can change the current mode by using the setenforce
command.man pages gives this as usage:
setenforce [ Enforcing | Permissive | 1 | 0 ]so you can execute
# setenforce 0to change SELinux currend mode to permissive.
No more reboots and downtime because of selinux!!!